Circa 2002, the high school uses a printing credit system to stop endless reels of paper going to waste, five cents per black and white page, fifteen cents for colour. Buried in the dark corner of the library, a geeky high school student waits at the entrance of the system administrators office. His printing credit is depleted and his business teacher insists the days work must be hard copy.
He waits with his five dollars in hand, knowing he is missing out on the daily lunchtime soccer match. Ten more minutes go by until the grumpy teacher who also acts as the system administrator walks past. He had heard horror stories from other students about the system administrator. Nervously extending his five dollars he asks “Can you please top up my printing credit?”.
The system administrator waves his hand to join him inside the office. Sitting down at the Windows 98 computer he starts navigating file shares. Curiously the geek looks over his shoulder wondering what he is looking for. A dialog appears on the screen asking for a username and amount. The system administrator looks back and asks for his username, “0passbe” the geek replied.
After entering the username, amount and clicking “Ok” the system administrator stands and says “All done”. The geek walks out of the office thinking “that wasn’t too hard, why can’t all teachers have access to that system”. He runs off towards the soccer match intending to join the loosing side for the challenge.
Few months go by and the bored geek is in business class. The teacher instructing students on the basic features of Microsoft Word. Yet his focus is on scouring every file and folder on the “C” drive, looking for anything interesting. After spending the better part of the class looking, he finds an interesting file he had not seen before “C:\logs\winlogon\a8n\login.log”. Opening the log file revealed hundreds of thousands lines of output.
“Five minutes left” the teacher yells, derailing his focus. With little time he inserts a 1.4 megabyte floppy disk into the machine with a clunk. Attempting to copy the file results in a “Not enough space” error. Reviewing the file he realises its 101 megabytes. Desperate to get a copy he ponders if compressing it will work. Firing up WinZIP he starts the compression process whilst packing his belongings.
The students are now leaving the classroom and the compression finishes at 1.38 megabytes. He listens to the rhythmic sounds of the floppy drive writing the file as the teacher hurries him along. “Just saving my work miss!”. File copied and floppy disk in hand he exits the classroom amazed at how raw text can be compressed.

That weekend, he copied and uncompressed the file on his AMD 1000 machine. Opening it with notepad he watched his machine struggle with the large file. Analysing the first few thousand lines he determined it to be a login profile activation log. There were large sections of duplication, but references to network drives like “X” and “Z”. These he hadn’t seen before and made note to try access them the following week. Growing tired of the repetitive log he gave up deleting the file to free up space for games.
During multimedia class the following week, he opened windows explorer and attempted to access the drives. Accessing “Z” produced an error, “Access denied”. This was odd he thought, when trying a non-existent drive it would error with “Drive is not accessible”. The drive must be present but access restricted. He had bypassed security measures of the school machines before, maybe he could again.
The Windows 98 machines had a myriad of security restrictions including the inability to use the right-click context menu. An “idiotic” measure in his opinion. Loading up his custom batch “de-restrictions” program he could turn off individual security restrictions. He had previously discovered that “regedit.exe” was restricted, yet the “reg” command was allowed via the command line. This would grant him modification privileges within the Windows registry allowing security restriction bypasses. After spending the class failing to gain access with a variety of techniques he abandoned the idea completely.

Months pass and another boring business class for our geek. The teacher, yelling instructions for the format painter feature, background noise to him. He is inspecting every esoteric feature of Microsoft Word looking for anything interesting. Opening the toolbar menu, to his surprise the options included a “Web” entry. Enabling it displays a URL toolbar a lot like Netscape Navigator or Internet Explorer. “Pointless” he ponders as the business class computers aren’t connected to the internet.
Always curious he starts typing in random characters and words with no luck. He wonders if file paths would work instead. Typing “C:\” and hitting enter, unexpectedly results in a windows explorer dialog. Remembering the inaccessible drives, typing in “Z:\” and enter……. pure shock. No “Access Denied” message just windows explorer with full access to the “Z” network drive. The thrill of bypassing the security restrictions was intense. Minutes pass, unable to process what happened he sat silently staring back at the screen.
By habit he started cataloguing every folder and file on the network drive. Sifting through every detail to understand the purpose of each item. With the class time up he couldn’t finish his work and it would be a few more days until he had computer access again. The library did have computers, even connected to the internet. Yet with the screens exposed to passersby, nosy librarians and a grumpy system administrator, he thought best to wait.
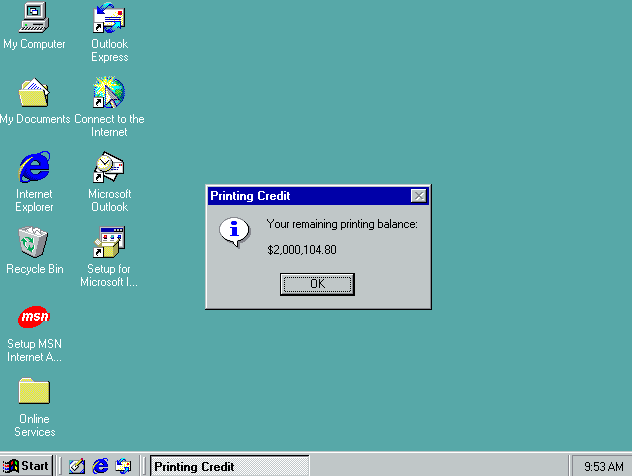
Multimedia class days later, he couldn’t wait to continue his work. Most of the drives contents were login scripts, printer drivers and empty folders. One item did catch his eye “Z:\help\pcredit\pcredit.exe”. Executing the program produced the same printing credit interface the grumpy system administrator had used. “Surely this wouldn’t work” he thought. Entering in his username and an amount he hesitated, hovering over the “Ok” button. Like most brash teenagers he had entered two million dollars, thinking better of it as someone might notice, he changed it to one hundred.
Selecting “Ok” the dialog box disappeared with no error message, “had it worked?” he thought. Anticipation skyrocketing as he double clicked the printing icon in the system tray, his balance reading “$104.80”. “It worked!” he yelled to no one in particular. To be sure he added another four hundred dollars before the end of class. Thinking to himself walking home, “should I tell someone?”. He wanted to show off to everyone, “look how good of a hacker I am!”. He could control any students printing credit with ease.
The following week, huddled over a library machine he showed his fellow geek friend. “Please don’t show anyone else” he asked wanting to simultaneously show off but keep it a secret. Forty-eight hours later, toner cartridges ran dry, printers jammed and endless reams of paper printed black. Millionaire printing credit students roamed the halls boasting as it all came undone.
Business class the next day, this time Microsoft Excel, a message appeared on his machine. It read “Your account has been locked, please immediately report to the system administrator!”. Once the school administration found out, all fingers pointed back to him, scared he made his way to the dark corner of the library.
The system administrator, now past grumpy demanded he write down every change he made. Twice he had to demonstrate the hack, as the system administrator couldn’t believe how easy it was. Months later he checked the hack still worked, finding the printing credit software had disappeared.
As you may have guessed by now, this is my first hacking story. I’ve not told this story for two decades. Documented now, not to brag but to educate prospective cyber security graduates about the hacker mindset. Being curious helped me learn information disclosure from comparing error messages, incident response by analysing log files and penetration testing fuzzing a URL toolbar.
My final year of high school, the grumpy system administrator was my information technology teacher. To his credit he was an amazing teacher and never held a grudge about the incident. Later I learned that printing credit could also be removed. Students were in tears, unable to turn in assignments as their accounts were depleted. A negative effect of my hacking that stays with me today.
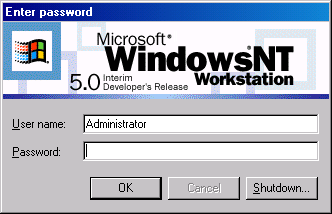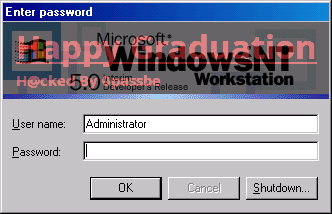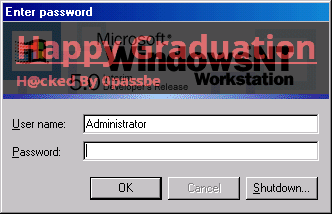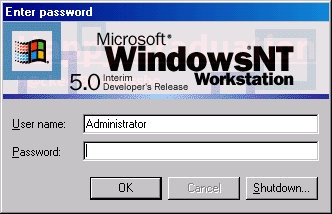
Six months before graduation I found the location of the Windows NT login banner image. This image, displayed at login on every machine throughout the school. I contemplated modifying the image (backing up the original) as a senior prank. Based on my previous experience I decided against showing off again.
Today would you describe this as a “righteous hack” or just a software bug? Either way it shaped the way I viewed computer security and taught me some valuable lessons.